Cryptocurrency scams ruining DeFi enthusiasm.
Many crypto enthusiasts will attest to the fact that decentralized finance (DeFi) represents a paradigm-shifting move that should be made in the field of finance.
Users of such a new space may have the opportunity to earn additional income while simultaneously contributing to the fulfillment of an overall community-driven goal.
Having said that, the innovations brought about by DeFi also have a few drawbacks. Scams involving cryptocurrencies, fraud involving Bitcoin (BTC), scams involving blockchain technology, and other wallet-threatening scenarios are rampant in this industry.
Just in the year 2021, fraud and theft in the cryptocurrency sector of the DeFi industry totaled more than $12 billion in crypto assets stolen from user wallets and exchange holdings combined.
Fraud involving cryptocurrencies took place in the remaining transactions, with dishonest parties taking advantage of users who were new to the sector. Part of this theft was caused by poorly programmed smart contracts and vulnerabilities in platform security.
It is imperative for the cryptocurrency industry as a whole that these cons and security loopholes be patched up before the crypto space can truly enter the mainstream.
Regrettably, it may be some time before the industry finds a solution to the problem of scams involving blockchain technology. This guide is intended to educate users on how cryptocurrency scams operate and how to recognize crypto scams until such time as the aforementioned time comes to pass.

How DeFi improves on traditional finance
Although the advantages of decentralization may be obvious to crypto enthusiasts, one cannot minimize the improvements in safety and accessibility that come with a decentralized financial network.
In spite of the current cryptocurrency scammer list of attacks, improvements to DeFi have the potential to bring about significant positive changes to mainstream finance.
When it comes to conventional banking and online financial platforms, there is only one primary point of contact: a server. Even though servers have multiple layers of security, there is very little that a company can do to prevent its servers from being hacked.
Theft gives an intruder access to valuable information such as passwords and addresses once they have gained entry.
On the other hand, decentralization disperses access to a variety of points of contact all over the world: the users. Users who are incentivized to hold parts of the distributed file sharing network on their connected device are typically referred to as nodes in the network.
In an ideal world, the greater the number of nodes that are connected to a network, the greater its level of security. A malicious actor would need to take control of 51% of the nodes connected to a network in order to launch an attack successfully. This is not an impossible feat, but it is highly improbable that it will ever be accomplished.
Accessibility is another feature that nodes bring to the table. Any individual is able to connect to and make use of any decentralized network of their choosing because a network is capable of being distributed globally via the devices of its users.
Users who are connected to the network are able to send funds and interact with the network in other ways, all without the barriers that are present in conventional financial transactions.
For instance, one is able to send money to a family member on the other side of the world almost immediately, freeing themselves from the fees and wait times that are associated with traditional international transfers.
In addition, there is no centralized authority that can obstruct the transactions of users or impose additional fees on them for reasons that are unclear.
The nodes in a DeFi network also keep full control over any changes or upgrades made to the network. In contrast to the traditional method, in which a centralized entity implements changes regardless of the wants and needs of users, the new method requires users to propose and vote on a change before it can be implemented.
In the event that a transaction on a network seems fishy, it is up to the users to vote on it and decide whether or not to undo it. Users are granted the authority to make decisions when decentralized systems are implemented.
Having said that, with all of the power that DeFi provides, that power comes with its own unique set of problems, such as fraud, human error, and malicious intent, as well as the obligation to find solutions to those problems.
Different ways hackers steal cryptocurrency
Many people find that the fact that blockchain technology gives power back to its users to be appealing on its own. It is not difficult to comprehend how users could become exhausted by centralized entities constantly telling them what to do.
However, with great power comes great responsibility, and the consequences can be extremely severe for DeFi creators who fail to live up to those responsibilities.
People use programmers to organize different capabilities and actions in order to build decentralized financial platforms. These platforms’ features are offered by these platforms. However, with human input comes the possibility of human error, and it is man-made errors that provide the opportunity for exploits.
Everywhere you look in the world of DeFi, new projects are being developed. Programmers who rush through their work are much more likely to introduce errors into their software, which is problematic given how important it is to be the first player in the game.
Considering that blockchain projects are entirely open source, which means that their source code can be accessed by anyone, individuals with malicious intentions will discover vulnerabilities and make use of them in order to steal funds and otherwise abuse a platform.
Even though bugs in the code can be found and fixed through the use of a third-party audit, the process is expensive, which is especially problematic in the emerging blockchain industry. There are a lot of projects that have trouble acquiring funding for even the most fundamental development.
It can be challenging to come up with the funds for an audit, which means that projects might move forward without a suitable code examination.
Platforms used in traditional finance, which are typically constructed using conventional code and servers, are not immune to human error or malicious attacks, of course.
However, traditional platforms are programmed using tried-and-true security methods that have been tested in the field for decades. Furthermore, traditional platforms do not face the challenge of having to program automated smart contracts.
Platforms that are based on blockchain technology do not have the luxury of having that kind of experience, which means that errors can appear out of nowhere, forcing developers to scramble to find a solution.
Then there’s the issue of having too much ambition. Some of the projects being developed are (relatively) straightforward token exchange platforms that make it easy for users to trade one token for another.
Some people are working toward the goal of tokenizing and automating the entire world in which we live in order to give users new ways to interact with traditional applications and services.
Building smart contracts that interact with other smart contracts, among other functions, means that there is bound to be an increase in the number of errors that occur. This is because platforms are becoming more comprehensive and have more diverse intentions.
Although decentralization is an essential component of decentralized finance, different platforms approach decentralization in varying degrees of seriousness.
If a project is too centralized, it exposes itself to the same dangers as conventional financial platforms that are hosted on conventional servers, despite the fact that it promises something entirely different.
As a consequence, malicious actors would most likely have a much simpler time attacking these platforms that are less decentralized.
How to spot and avoid cryptocurrency and digital currency exchange (DeFi) scams
Even though it is impossible to stop fraud and theft in the cryptocurrency industry as a whole, the following common scams should be on the watchlist of every DeFi trader.
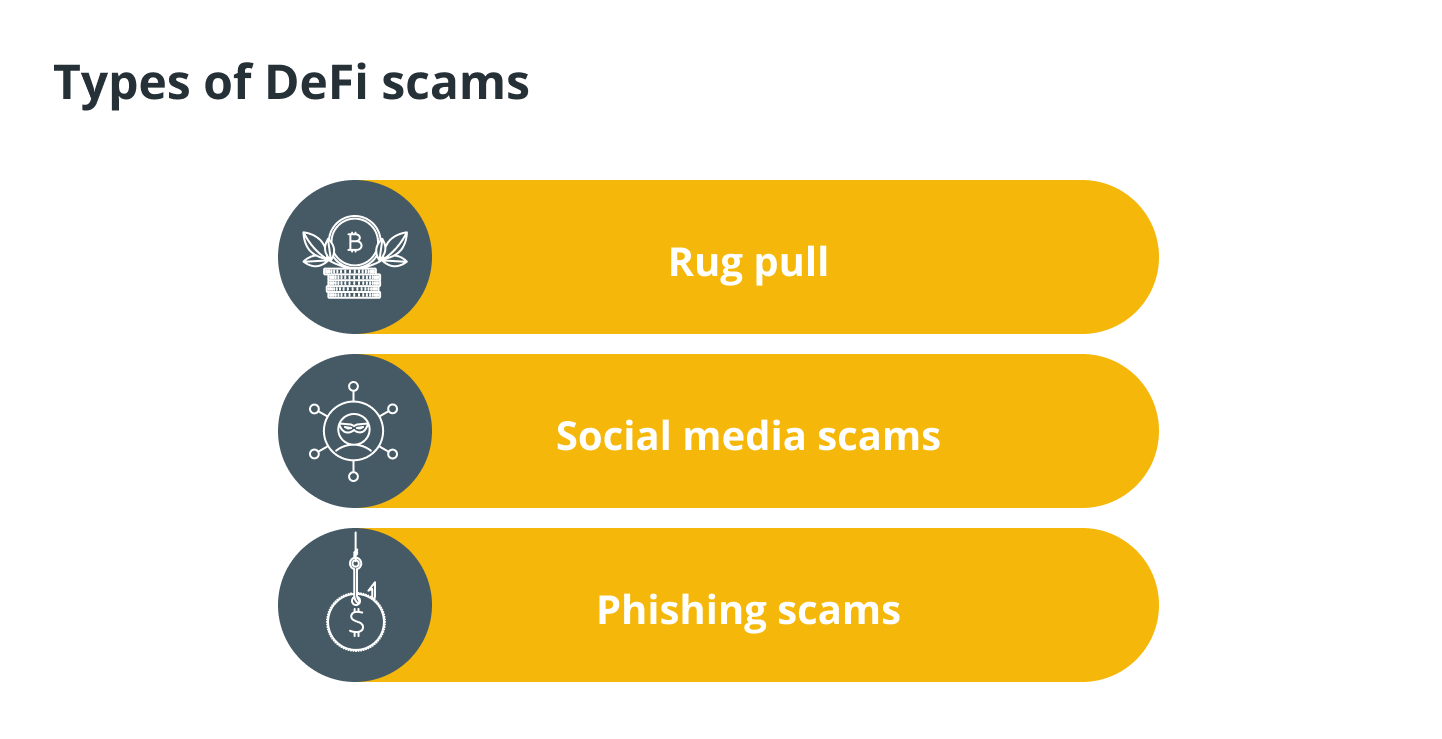
A rug pull
Rug pulls are one of the most common types of cryptocurrency scams that can be found in the DeFi space. However, they are also one of the easier scams to identify for those who are aware of what red flags to look out for.
When developers promote what seems to be an exciting and revolutionary project, they are engaging in what is known as a “rug pull.” They amass a following and secure financial backing from investors amounting to hundreds of thousands, if not millions, of dollars.
After that, at some point in the future, these developers will simply sell the tokens and vanish with the money. These property developers never intended to use the money from the investors to build a project. They were only interested in carrying out a scam.
Suddenly, investors will have nothing to show for their investment, and the project will be scrapped. Investors, in a sense, have the rug yanked out from underneath them.
It is possible to detect a con artist from a mile away if one pays attention to the relationship that a developer has with the communities that they serve, in addition to the plans that they have for token distribution.
Suppose a project does not specify any kind of lock-up period for tokens, particularly a lock-up period for the developers. In that case, the teams involved can do whatever they want with tokens at any time.
It is in everyone’s best interest to align with projects that have detailed token lock-up periods, as this will prevent developers from fleeing with funds. These projects will, in general, maintain a high level of transparency with their respective communities, providing regular updates as well as an overarching strategy. (A pump and dump scam is very similar to a rug pull, despite the fact that both are not unique to DeFi.)
When a project is described as being “unruggable,” it indicates that the development team has not contributed a significant number of tokens to the project.
Unruggable is a term that can be applied to a project, for instance, if it does not have the significant hallmark of team-held tokens that could be taken in a rug pull or exit scam.
Another way to determine whether or not a project is unruggable is to examine whether or not the team involved gives up control of any tokens, such as those acquired during a presale.
Social media scams
Scam accounts that impersonate various celebrities can be found all over Twitter. Some of these celebrities are associated with the cryptocurrency industry, while others are not.
In any case, these impersonators will conduct outreach to crypto enthusiasts in order to inform them about their new project. They may also pretend to hold giveaways and competitions in which users are required to send funds to a specific address.
It is not difficult to determine whether or not these accounts are genuine. For instance, in comparison to the millions of followers that the real celebrity account has, an impersonator will most likely only have a few thousand of their own followers.
These accounts frequently contain basic typos as well as grammatical and spelling mistakes. Regardless, one should never engage in conversation with a Twitter account or send money to an account they find there in the first place.
A cryptocurrency fraud scheme that appears to be so straightforward may sound ridiculous, but unfortunately, it happens every day. In the year 2020, dishonest individuals hacked into the legitimate celebrity Twitter accounts of famous people in order to send out fraudulent tweets.
Phishing Scams.
Phishing is a form of online fraud that has been around almost as long as the internet itself. In this con, con artists pose as legitimate businesses in order to acquire sensitive information about their victims.
Phishing for DeFi tokens is typically carried out through the medium of email, with the fraudulent actor pretending to be a representative from a trading platform or protocol.
A con artist will feign an error, such as “your account has been compromised,” in order to steal your money. Please forward us your email as well as your password so that we can secure it. Asking the victim for their wallet addresses and passwords or demanding that the victim send money are both examples of such underhanded tactics.
Phishing emails may contain links to fake websites that look very much like an existing platform. These websites are designed to trick victims into entering their personal information so that the scammers can steal it.
Checking the email address of a contact is an absolute necessity in order to avoid falling for phishing scams related to blockchain technology. In many cases, the email will contain a string of meaningless characters rather than the real name of the website.
In any other case, you should never click on a link contained in an email that looks suspicious. Manually navigating to the website of a platform and double-checking the URLs can help you avoid falling victim to scams like these in the event that there is a genuine security issue.
For instance, confirming that the URL in question possesses a https security certificate and that the URL in question has been spelled correctly.
The general precautions for security that should be taken
It is vital to keep an eye out for the scams and frauds that have been mentioned previously within DeFi; however, there are some generalized methods that can assist one in remaining off of a cryptocurrency scammer list.
2Factor Authenticator (2FA)
No matter which sector of the DeFi ecosystem an individual decides to invest in, every platform ought to have at least one method of two-factor authentication. Two-factor authentication, also known as 2FA, is a method of account security that necessitates the use of a text message or email after the input of a user’s password.
Even if a malicious actor obtains access to a user’s password, they still won’t be able to break into an account unless they also have access to the user’s mobile device or email.
Use a hardware wallet
Users are able to keep their private keys secure by storing them in hardware wallets, which are external devices. The development of the decentralized finance industry has led to an increase in the number of decentralized applications (DApps) that are compatible with hardware wallets. This allows users to store their assets in a safe location while still having easy access to the decentralized finance platforms of their choice.
Even if a platform provides its users with a wallet, it is difficult to recommend that users store their assets in an online wallet. When users store their assets online, they expose their money to the risk of being stolen.
Defi attacks frequently result in the loss of millions of dollars across the accounts of thousands of users. Users can increase their level of protection by one notch by preventing a platform from having access to the funds that they control.
Always Investigate the Community
When a DeFi project is successful, it typically cultivates a thriving community that is comprised of both active users and developers who communicate with one another. Communication of this kind is absolutely necessary in order to construct a platform that is risk-free and that everyone can enjoy.
Having said that, if there is a project that has developers who are not very active or vocal, it is possible that they are plotting a rug pull or some other type of scam. Crypto enthusiasts will almost universally agree that it is in your best interest to become familiar with the developers behind a project.
If a group hides their plans from their community and does not engage in open dialogue about what they are doing, there is reason to suspect that they have nefarious objectives.
Before forming an opinion on something, it is recommended first to become involved in endeavours that already have thriving communities and, even then, to conduct additional research in this area.
One more thing that can be done is to pay attention to listing platforms and the reasons why they might or might not include a token. If a listing platform does not accept a token, then you should probably avoid investing in it.