Detailed analysis of the benefits, drawbacks, and distinctions
Although the history of Bitcoin (BTC) transactions are sequenced in a secure manner using proof-of-work (PoW), the process uses a significant amount of electricity and has a limited capacity for the number of simultaneous transactions it can process. As a direct consequence of this, new consensus mechanisms that prioritize the method that uses less energy have come into existence, with the proof-of-stake (PoS) model being one of the most prominent examples. The use of these consensus mechanisms makes it possible for computer networks to work together while maintaining their safety.
In order to perform their intended functions, blockchain networks will need to find solutions to a few problems. Decentralized cryptocurrency networks, for example, have the responsibility of ensuring that no participant in the network wastes money by spending it more than once. This is necessary because there is no central authority, such as a bank or a FinTech company (like PayPal), to act as a go-between. Additionally, the consensus mechanism stops the network from being sidetracked by a hard fork, which is a potential threat.
In contrast, the board of decision-makers or regulators in a centralized organization, such as a bank, are the ones who control the activities in question. In contrast, cryptography relies on a community and for that reason, the blockchain needs to arrive at a decision before it can verify transactions or blocks.
Proof-of-work and proof-of-stake are the two main consensus mechanisms that are currently being used by decentralized finance (DeFi) projects to cryptographically obtain consensus on cryptocurrency networks. Proof-of-work was developed in 2010 and proof-of-stake in 2011. When Satoshi Nakamoto was developing Bitcoin (the first cryptocurrency), he and his team needed to devise a method that would allow transactions to be validated independently of the intervention of a third party. To accomplish this, they utilized a consensus mechanism known as proof-of-work to enable networks to reach a mutual understanding regarding the legitimacy of particular transactions.
On the other hand, proof-of-stake, also known as PoS, is a relatively new consensus mechanism that is used to power more recent cryptocurrency projects. Some projects jump right into the PoS phase, while others are making the switch from the PoW phase. Building a PoS consensus network right away, however, is a significant technological issue, and it is not as simple as using PoW to gain network consensus. Using PoW to gain network consensus is the more straightforward option.
What is meant by “proof of work”?
The concept of proof-of-work was first put forward in 1993 with the intention of combating spam emails on a network and denial-of-service attacks. When it came time to validate new blocks in the Bitcoin network in 2008, Satoshi Nakamoto was the one who brought the Proof of Work (PoW) concept to widespread attention.
Proof-of-Work relies on the ability of network users to demonstrate that a certain computational task has been completed. In order to solve a mathematical equation, a piece of computing power that is referred to as a node is used, and as soon as the equation is solved, a new block is added to the chain and it is validated. A physical device, such as a personal computer, that is part of a network of other devices and has the ability to receive, send, or forward data is referred to as a node in this context.
The individual who deciphers a mathematical puzzle in the shortest amount of time will be rewarded with newly minted cryptocoins and will create a cryptographic link between the current block and the block before it. Mining is the term given to this process, and people who solve problems are called miners. A blockchain’s integrity is preserved for the benefit of all participants thanks to the collaborative efforts of its users. In addition, the computational challenge of solving this puzzle is known as a proof-of-work in and of itself.
How does PoW work?
A blockchain is a distributed ledger that stores information in the form of a chain of blocks that are organized in chronological order according to a transaction order that is referred to as blockchain ordering. The first block in a Proof-of-Work blockchain is called the genesis block, also known as block zero. This block is hardcoded into the software. This block, by its very nature, does not refer to any block that came before it. The subsequent blocks that are uploaded to the blockchain always include a reference back to the blocks that came before them and contain a ledger copy that is both complete and up to date.
PoW algorithms decide who gets to add the new entries to the ledger by holding a race to see who can submit the most valid blocks that adhere to the rules of the network. This race takes the form of a competitive competition in which participants or miners are encouraged to expend computational resources in order to submit legitimate blocks. The ledger is responsible for keeping track of all transactions and organizing them into blocks in a sequential order. This ensures that no user can spend the same amount of money more than once. The distributed nature of the ledger helps prevent tampering by enabling other users to quickly reject an altered version if it is discovered.
Hashes, which are long strings of numbers that act as proof-of-work, are what users actually use in practice to determine whether or not data has been tampered with. The hash function is a one-way function, which means that it can only be used to check that the data that generated the hash is identical to the data that was initially input into the function.
After that, nodes examine transactions, look out for instances of double spending, and determine whether or not the proposed blocks ought to be added to the chain. Double spending refers to the practice of making payments using the same currency twice in order to trick the person who is supposed to receive those funds. The practice of double spending would wreak havoc on the network and remove one of its most valuable features, which are immutability, decentralization, and trustlessness. Those features would be rendered useless.
Due to the fact that altering any part of the blockchain would necessitate re-mining all subsequent blocks, double spending is rendered extremely difficult by the use of proof-of-work. It is impossible for users to monopolize the processing capacity of the network due to the high cost of the machinery and power required to carry out the hash functions.
In addition, a PoW protocol combines cryptography with computational power in order to generate consensus and ensure the legitimacy of transactions that are recorded in a blockchain. This is done in order to secure the legitimacy of transactions.
During the process of hashing, which produces new blocks, miners compete with one another to determine which mathematical problem yields the correct answer. Miners accomplish this goal by attempting to deduce the contents of a hash, which is a string of seemingly random numbers. A cryptographic hash (for example, SHA-256) is a type of signature that can be applied to text or data files. For a text, SHA-256 provides a nearly-unique 256-bit (32-byte) signature.
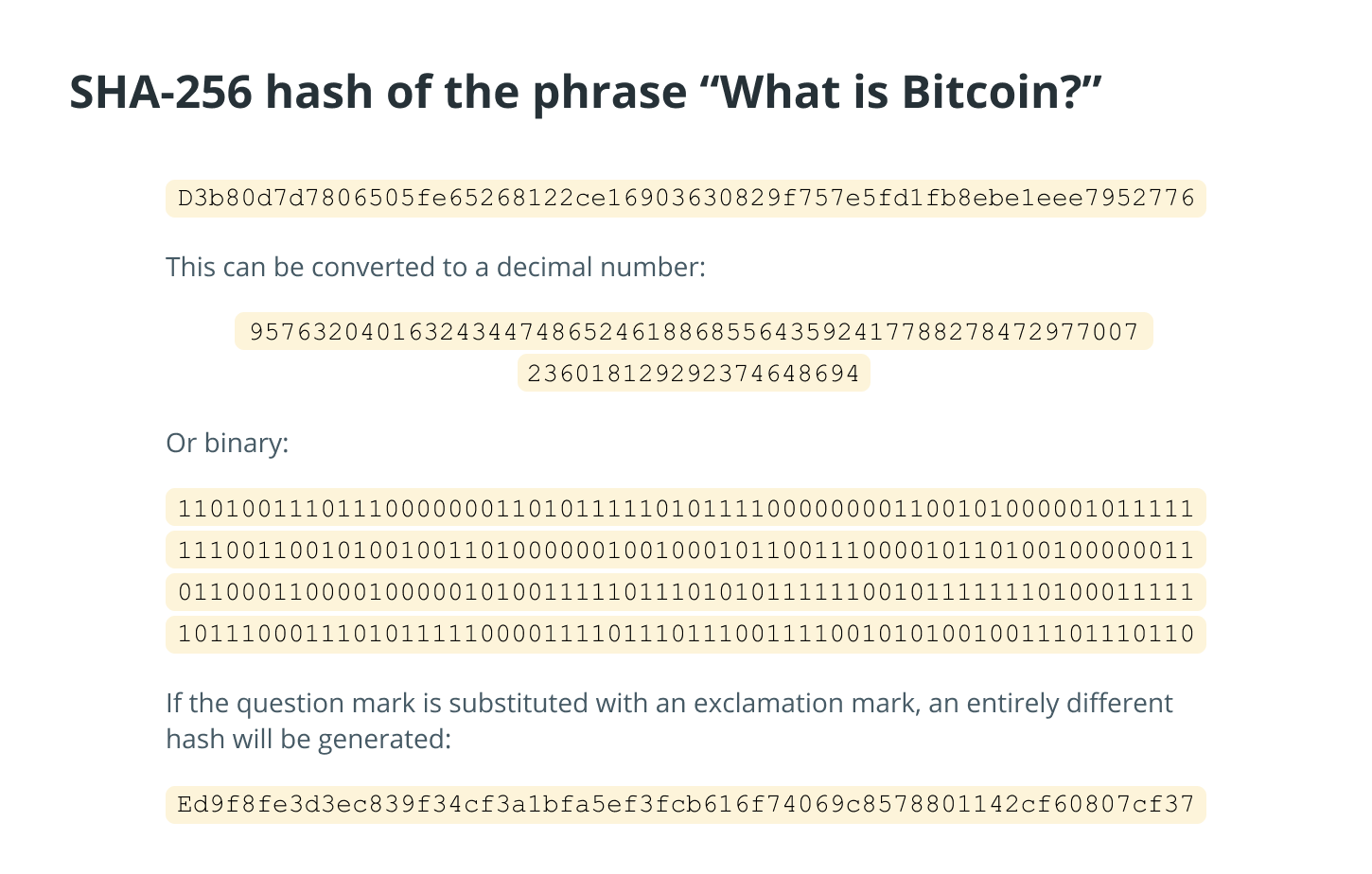 Hash values must produce a result that, when combined with the data contained in the block and run through a hash function, generates a result that satisfies the requirements specified by the protocol.
Hash values must produce a result that, when combined with the data contained in the block and run through a hash function, generates a result that satisfies the requirements specified by the protocol.
The miners who were successful in obtaining the hash then communicated it to the network so that other miners could validate whether or not the answer was accurate. In the event that the response is correct, the block will be added to the blockchain, and the miner will receive the reward for the block. As an illustration, the reward for mining a Bitcoin block at the moment is 6.25 Bitcoin.
The perks and drawbacks of the PoW
The benefits of PoW
In Proof of Work systems, miners are required to spend a significant amount of money on electricity in order to solve difficult mathematical puzzles and process blocks for the network. It is called mining, and it is the process of verifying transactions that generates digital assets. The electricity is used to power the machines that generate digital assets. In addition, the expenditure of energy is essential to the security of the network because it enables the network to maintain an accurate record of transactions and adhere to a predetermined, credible monetary policy.
In addition, the network is protected because in order to commit fraud against the chain, a malicious actor would need to take control of 51% of the computing power that the network possesses. In a system that relies on proof-of-work transactions, when a blockchain experiences a fork, miners are forced to decide whether they will join the newer forked blockchain network or continue to support the original blockchain.
In order to support both blockchains, a miner would need to divide the computational resources they possess between the two distinct chains that resulted from the fork. Because of this, proof-of-work systems naturally prevent constant forking by providing miners with an economic incentive to choose the path that does not wish to cause harm to the network. This encourages miners to choose the path that is most beneficial to the network.
Because of these characteristics, game theory, in which miners are required to act strategically in order to maximize the returns on their investments, is a useful framework. People, much like bounded rationality states, will invariably opt for the solution that is the least complicated. The transition to a more modern chain makes things more difficult. As a result, game theory assists oligopolies in preventing internal corruption and in making decisions that are rational.
Contrary to the PoW
In spite of the benefits discussed above, Proof of Work can be quite expensive and wasteful in terms of the resources it uses. Miners have to deal with a wide variety of costs, including the purchase of expensive new equipment that has a short lifespan. Depending on the location of the miner, the mining operation will typically generate a significant amount of heat and may rack up exorbitant electricity costs. In addition to this, the transaction fees for the system skyrocket when the network is in an overloaded state.
Additionally, if you are susceptible to a 51% attack or if you are not on the most significant coin holder for any interchangeable hashing algorithm, individuals on a larger coin may turn their hardware against you and take you out, at which point you will no longer be able to earn an incentive. This can happen even if you are not on the most significant coin holder.
How does proof-of-stake work?
In 2011, a fresh strategy to address the inefficiencies of the PoW consensus mechanism and reduce the quantity of computational resources needed to run the blockchain network was proposed on the Bitcointalk forum. This idea is predicated, not on the completion of concrete tasks, but rather on the possession of a demonstrable stake in the ecosystem.
To put it another way, in order to validate transactions on the cryptocurrency network, a user need only demonstrate that they own a specific quantity of cryptocurrency tokens that are native to the blockchain. This is the only requirement for validating transactions. The proof-of-stake consensus mechanism is a type of consensus mechanism that is utilized by blockchain networks in order to accomplish the task of achieving distributed consensus.
For example, miner A puts 30 coins on the line, miner B puts 50 coins on the line, miner C puts 75 coins on the line, and miner D puts 15 coins on the line. In this particular scenario, miner C would be given priority to write and validate the block that comes after it. Miner C will be responsible for collecting transaction fees, also known as network fees, in contrast to the block reward that is awarded in proof-of-work algorithms.
How does PoS work
The first block in a proof-of-stake blockchain is referred to as the genesis block. This block is also hardcoded into the program. The subsequent blocks that are uploaded to the blockchain always include a reference back to the blocks that came before them and contain a ledger copy that is both complete and up to date.
Miners in a PoS network do not have to compete with one another for the right to add blocks. The process of extracting the blocks from the ground is often referred to as “mining,” but more commonly as “minting” or “forging.”
In contrast to PoW blockchains, PoS blockchains do not impose any restrictions on who can propose blocks based on the amount of energy they consume. Mining is no longer necessary thanks to innovative consensus mechanisms such as proof-of-stake, which do away with the need for blockchains to be powered by proof-of-work.
The proof-of-stake system has a number of advantages over the proof-of-work scheme, one of which is increased energy efficiency due to the fact that mining blocks does not require a significant amount of energy. In addition, the production of new blocks does not necessitate the use of cutting-edge technology. Because of proof-of-stake, the network now has a greater number of nodes.
The presence of a greater number of nodes in a network contributes to the development of governance norms that offer a higher level of resistance to centralization. This is made feasible in PoS systems by the increased degree of hardware independence that is present in those systems. As a consequence of this, proof-of-stake is typically regarded as the consensus algorithm that is least likely to result in the centralization of the network.
Users of a Proof-of-Stake (PoS) network who want to be included in the process of adding blocks to the blockchain must stake, or lock, a specific amount of the network’s cryptocurrency in a one-of-a-kind contract. This allows the user to be eligible for inclusion in the process. The amount of crypto assets that a user has staked is directly proportional to the probability that they will be selected to produce the subsequent block. Users who engage in malicious behavior risk having their stake confiscated as a consequence of their behavior.
PoS may make use of other determining factors in addition to pure randomization, such as the amount of time a node has been actively staking its funds, which may not always work to the advantage of the nodes with the most wealth. In a manner analogous to the PoW mechanism, the term “block reward” refers to the network fee that is presented by the blockchain to the individual who is responsible for the submission of a valid block.
In PoS, the selection of blocks is determined by who owns the coins in circulation. Because of this, staking services are provided by exchanges to enable users to have their cryptocurrency staked on their behalf in exchange for more consistent rewards. Staking pools allow multiple stakeholders to pool their computing resources and increase their chances of being rewarded. Staking pools can be joined by multiple stakeholders. To put it another way, during the process of verifying and validating new blocks, they combine their stakes with those of other users in order to increase the likelihood that they will receive block rewards.
PoS: the benefits and drawbacks
The Positives of Using PoS
The problem of significant losses of valuable energy resources has been taken into consideration in PoS. In addition, proof-of-stake (PoS) systems are significantly more scalable than proof-of-work (PoW) systems, and they also approve transactions much more quickly. Scalability refers to the ability of a system to perform more transactions per second (TPS) than certain existing systems through the modification of the system’s parameters or the change in the mechanism by which it reaches consensus.
The PoS network achieves scalability by establishing a consensus before blocks are constructed. This enables the network to process thousands of requests per second with a latency spike of less than one millisecond.
Cons of using PoS
The Proof-of-Stake protocol, on the other hand, comes with its own unique set of challenges. To give one example, the network is still susceptible to being dominated by the token holders who hold the most significance. This gives early adopters and people who already have the most money an advantage over others.
Due to the fact that this idea is still in its infancy, the cryptocurrency community may not yet be aware of any potential drawbacks it may have. In contrast to the proof-of-work model, this paradigm does not have a track record of successful applications. In addition, proof-of-take systems do not necessarily discourage the practice of forking by themselves. When a blockchain splits, a validator will get a duplicate copy of their stake on the newly forked blockchain.
The predicament known as “nothing at stake” occurs when a validator gives their stamp of approval to both sides of a fork. This gives the validator the ability to potentially double-spend their coins and collect twice as many transaction fees in return.
A comparison of proof-of-work and proof of stake systems
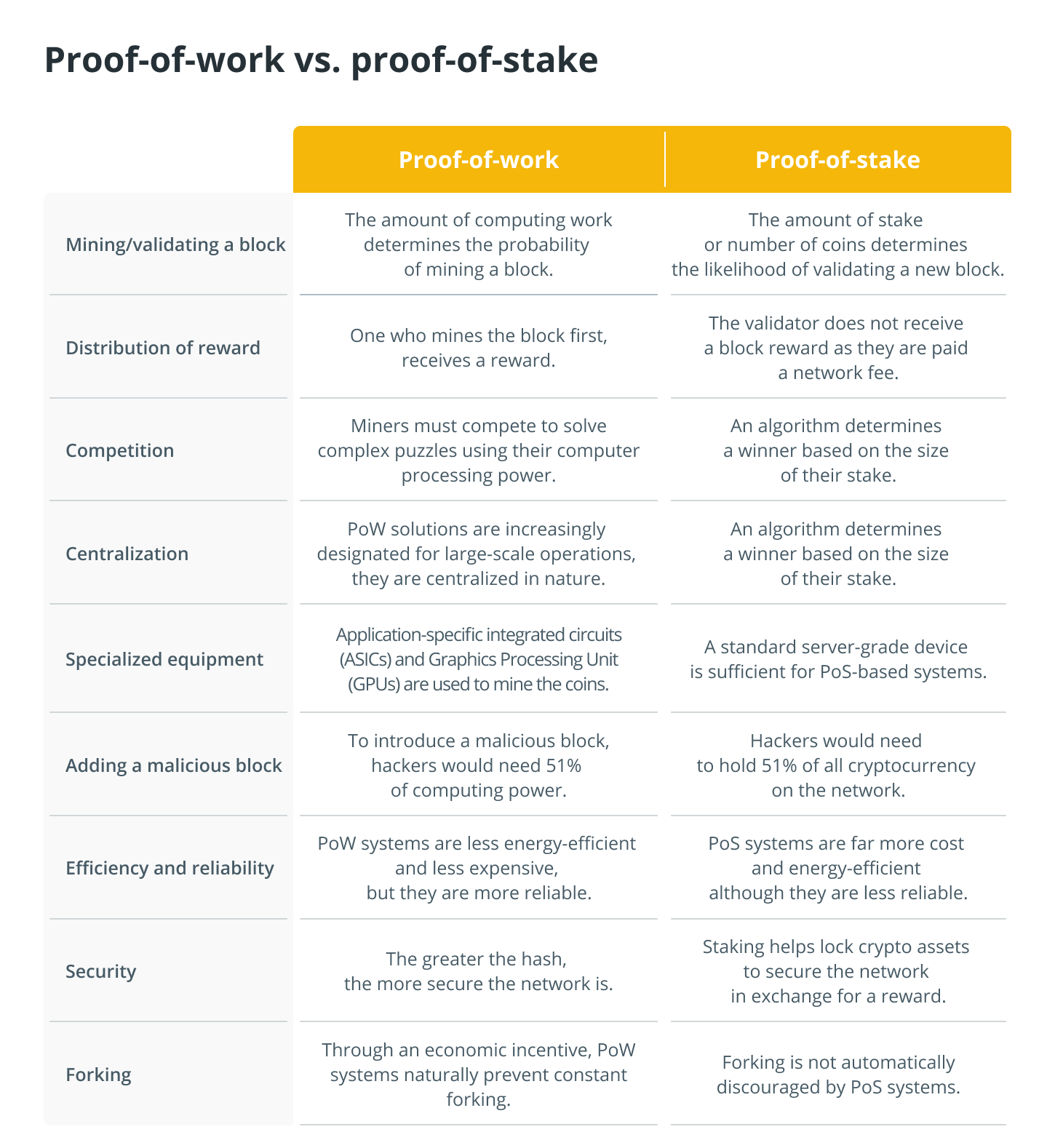
The explanations that came before this one make it abundantly clear that both types of consensus mechanisms have both advantages and disadvantages. They all have the same overarching goal as the ones listed above, but they go about accomplishing that goal in a variety of different ways.
The manner in which they delegate and are rewarded for transaction verification is the most important distinction between the various consensus mechanisms. The table that follows provides an explanation of the other differences.
 When should Proof of Work or Proof of Stake be Used?
When should Proof of Work or Proof of Stake be Used?
Because it reduces the centralization of the entities that are responsible for validating transactions, the consensus mechanism is an essential component of the distributed design of a blockchain network. It is necessary to have a fully functional consensus mechanism in order to maintain the immutability, trustlessness, and distributed nature of a blockchain network.
The requirements of a network will determine the kind of consensus that must be reached. Proof-of-work is one example of a requirement that is necessary for the prevention of fraud, the establishment of security, and the development of trust in a network. Because Proof of Work provides such strong protection, miners, also known as independent data processors, cannot be led astray regarding a transaction. Proof-of-work is a method that increases the difficulty of changing data over time while simultaneously securing the transaction history of a crypto asset. This makes it more difficult to alter the data.
The requirement that a participating node demonstrate that the work has been completed and submitted qualifies it to add new transactions to the blockchain. This prevents any malicious activity from being added to the ledger.
PoW helps determine which version of the blockchain is the most authoritative even if there are multiple copies floating around the network. Last but not least, proof-of-work is necessary for developing a distributed clock that enables miners to freely enter and exit the network while still keeping the same rate of operation.
Using a mechanism that is based on PoS can also have significant effects on the performance of a network and its level of security. When a high transaction speed for on-chain transactions per second as well as actual network transfer settlement is required, Point of Sale (PoS) technology is utilized. Furthermore, validators are likely to possess significant amounts of the network token, which provides a financial incentive for them to maintain the chain’s integrity and prevent potential breaches.
However, there are some concerns regarding the level of protection provided by point-of-sale and proof-of-work systems against potential dangers. In order to verify the legitimacy of transactions in a risk-free manner, a validation system known as proof-of-space or the Chia project has been developed. Chia addresses some of the centralization problems that plague proof-of-work (PoW) and proof-of-stake (PoS) blockchains by utilizing a proof-of-space and proof-of-time consensus mechanism.